A modular malware with worm capabilities exploits known vulnerabilities in servers running ElasticSearch, Hadoop, Redis, Spring, Weblogic, ThinkPHP, and SqlServer to spread from one server to another and mine for Monero cryptocurrency.
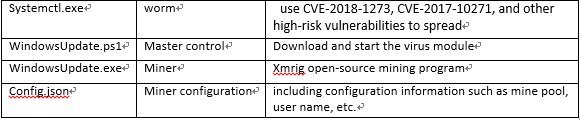
Systemctl.exe, the worm module of the malware named PsMiner by the 360 Total Security researchers, is a Windows binary written in the Go language which bundles all the exploit modules used to hack into vulnerable servers it can find on the Internet.
Besides the exploits, PsMiner’s worm module also has the capability to brute force its way in, whenever it finds targets that uses weak or default credentials, as well as crack user credentials using an additional brute force password cracking component.
Once it manages to infiltrate a victim’s computer, PsMiner will execute a PowerShell command which downloads a WindowsUpdate.ps1 malicious payload, the malware’s master module designed to drop the Monero miner as part of the final infection stage.
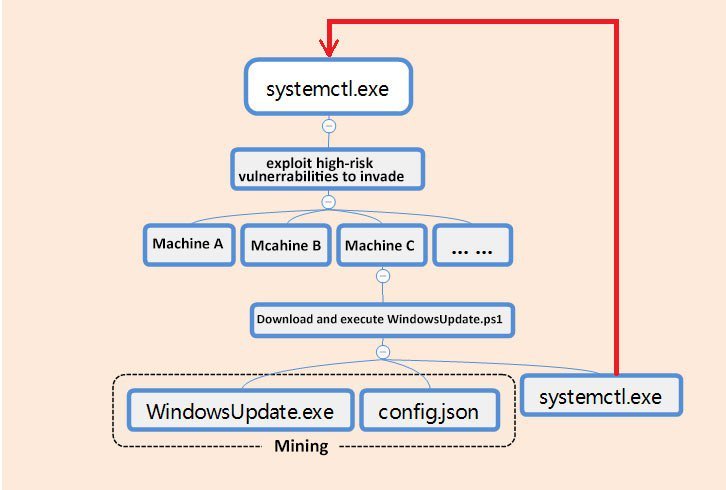
The malware will also copy the malicious WindowsUpdate.ps1 script to the Windows Temp folder and will create an “Update service for Windows Service” scheduled task designed to re-launch the main malware module every 10 minutes to help it keep persistence on the compromised system.
During the last stage of the infection, PsMiner will download and launch the open source Xmrig CPU miner, used to mine for Monero cryptocurrency with the help of a custom mining profile.
While the worm capabilities it uses to spread between its victims and the way it uses living-off-the-land (LotL) techniques to further compromise its targets and achieve persistence are quite effective, not the same thing can be said about the profits this campaign was able to collect for its masters.
As the 360 Total Security researchers say in their report, “Inquiring about the relevant transaction records, we found that in just two weeks, the miner accumulated a total of about 0.88 Monroe (sic) coins.”
Cryptojacking still a threat
According to Symantec’s 2019 Internet Security Threat Report, the use of malicious PowerShell scripts increased by a whopping 1,000% during 2019, closely following the overall trend of cybercriminals moving to LotL techniques to avoid being detected while infiltrating their targets’ systems.
Even though the use of cryptojacking malware followed a downward trend during 2018, it’s still in the arsenal of threat actors as shown by PsMiner, by a batch of eight Microsoft Store apps found to be dropping malicious Monero cryptomining scripts, and by hundreds of vulnerable and exposed Docker hosts actively being abused in cryptojacking campaigns.
Additionally, a new Backdoor Trojan dubbed SpeakUp which drops XMRig miners on its victims and a new coinminer malware strain using the XMR-Stak Cryptonight cryptocurrency miner were detected targeting servers multiple Linux distributions.
Cryptocurrency mining malware also affected ten times more organizations than ransomware did during last year, while and more and more malware families have begun to merge in new capabilities targeting cryptocurrency within their arsenal, as detailed by a Check Point Research report.
Previous Articles:
- Bumble Bee Uses Blockchain To Trace Fish From Ocean To Table
- Bitcoin Will Soon See ‘Bull Cross’ in First Since August 2018
- Old School Altcoins Can’t Stop Popping
- US Marshals Service Seeks Manager For Confiscated Cryptocurrency
- The SEC’s Crypto Czar Is Hitting the Road – And She Wants to Meet You
