ESET antivirus researchers have announced the discovery of an unknown trojan malware family that spreads through malicious torrents and uses multiple methods to extract as many cryptocurrencies from its victims as possible while remaining undetected.
ESET named the threat KryptoCibule and, according to its telemetry, the malware appears to target mainly users in the Czech Republic and Slovakia.
Triple Threat
This malware poses a triple threat to cryptocurrencies. It uses the victim’s resources to mine currencies, attempts to infiltrate transactions by replacing wallet addresses on the clipboard, extracts files related to cryptocurrencies, and develops multiple techniques to remain undetected. KryptoCibule makes extensive use of the Tor network and BitTorrent protocol in its communication infrastructure.
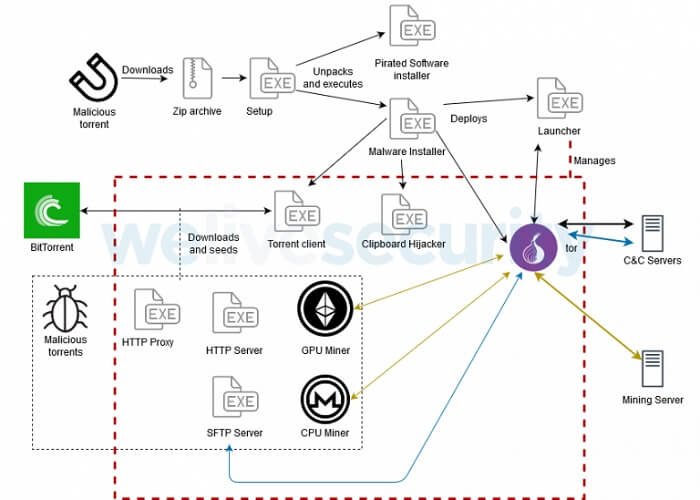
ESET has identified many versions of KryptoCibule, allowing them to study its evolution from December 2018 to the present day. The malware remains active, new features were added during its lifetime and is under constant development.
Victims Located in Czech Republic and Slovakia
Most of the victims are located in the Czech Republic and Slovakia, and this reflects the user base of the site where the infected torrents are located. Almost all malicious torrents were available on uloz.to, a popular file-sharing site in both countries.
In addition, KryptoCibule specifically checks for the presence of ESET, Avast and AVG security products.
More technical details about KryptoCibule can be read in the relevant blogpost on WeLiveSecurity.
Previous Articles:
- Crypterium Signs New Partnership with Apple Pay, Unveils its Virtual Card
- Top 5 Crypto Invoice Services for Making Business Administration Simpler
- Data-Intensive Sector Has A Lot More To Explore With Blockchain Technology
- 8 Useful Browser Extensions for Cryptocurrency Users
- 4 Tips on How To Succeed on Bitcoin Trading
