KEY TAKEAWAYS
- Bcrypt is a password hashing function that transforms plain passwords into unique alphanumeric sequences.
- It is a one-way process, ensuring that passwords cannot be reverted back to their original form.
- Bcrypt combines the password, salt, and cost factor to derive a unique hash, making it more secure than other hashing algorithms.
- Bcrypt is widely used in applications like WordPress, OpenBSD, and web development frameworks for secure password storage.
Imagine you’re a vault keeper, guarding valuable information.
In the digital world, bcrypt is your unbreakable lock. It’s a superior password hashing function that transforms plain text into complex, encrypted data. Born from Blowfish cipher, bcrypt is crucial for safeguarding sensitive information.
In this article, we’ll analyze what is bcrypt, how it works, compare it with other hashing algorithms, and explore its practical applications.
You’re about to unlock the power of bcrypt, enhancing your digital security knowledge.
Table of Contents
What is password hashing?
In the realm of cybersecurity, password hashing is a method you’ll often encounter, as it’s a technique that transforms your plain password into a unique sequence of numbers and letters.
To put it simply, password hashing is like a cryptographic blender. You input a password, and the algorithm scrambles it into an unrecognizable series of alphanumeric characters.
This process is one-way, meaning once your password is hashed, it can’t be reverted back to its original form.
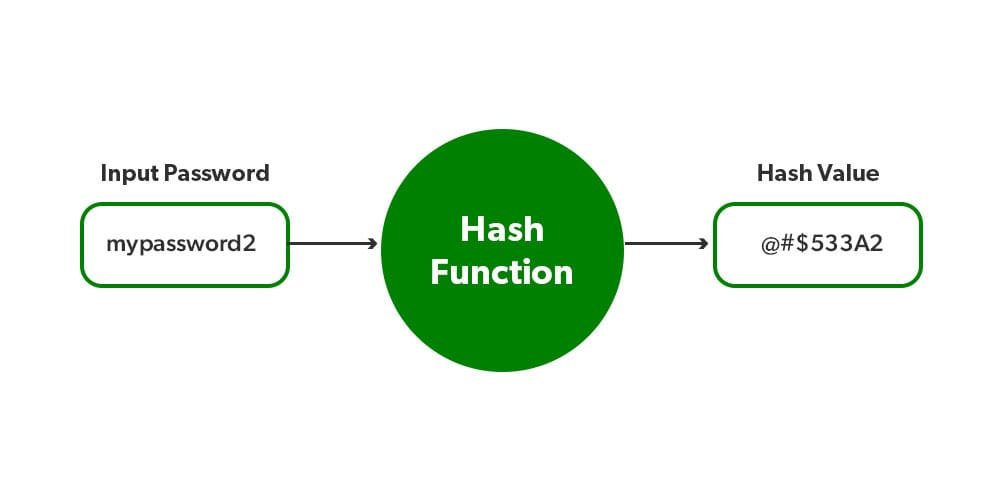
This ensures that if a data breach occurs, the attacker can only access the hashed version of your password, which is practically useless without the original password.
Think of it as a secret code that can’t be cracked.
Popular algorithms such as bcrypt and SHA are often used in password hashing. These algorithms add an extra layer of security by inserting a ‘salt’, a random bit of data, into your password before hashing it.
This makes it even tougher for attackers to misuse your data, as they’d need to know the exact ‘salt’ used to stand any chance of decoding the hash.
What is Bcrypt password hashing function?
To ensure the utmost safety of your passwords, you’ll often come across bcrypt, a cryptographic hash function designed specifically for password hashing and safekeeping.
Bcrypt was created back in 1999 by Niels Provos and David Mazières.
The name ‘bcrypt’ originates from the blending of ‘b’ for “Blowfish“, a cipher algorithm it uses as its base, and ‘crypt‘, the hashing function used by the Unix password system.
Bcrypt works by taking your password string and combining it with a salt and cost to derive a unique hash.
The salt, a random value, is added to your password to thwart rainbow table attacks, while the cost, a numeric factor, determines the number of hashing iterations. The resulting hash string is then prefixed with bcrypt’s specific algorithm identifiers.
Despite being slower compared to other algorithms, bcrypt’s strength lies in its resistance to brute-force attacks — the slower the hash function, the more secure your passwords.
Thus, bcrypt fulfills its purpose: to transform your passwords into complex, unique hashes, ensuring their safe storage and your peace of mind.
How bcrypt works: How bcrypt hashes passwords?
Now, let’s see how bcrypt actually hashes your passwords, transforming simple text into a complex code.
Bcrypt takes your plain password and first appends a randomly generated string, known as a “salt”. This additional data disrupts precomputed tables used by attackers for reverse-engineering your password, enhancing security.
Next, bcrypt determines the time it’ll take to generate a hash via a cost factor.
Here’s where it gets technical: the cost factor, a numerical representation, defines the number of times the hashing function is executed.
Higher cost factors mean more processing time, which makes the hash harder for intruders to crack.
Once the “salt” and cost factor are determined, bcrypt starts the hashing process.
It combines the salt and password, runs the hashing function as many times as the cost factor dictates, and produces a unique hash.
This hash is prefixed with an algorithm identifier and the cost factor. The final bcrypt hash consists of the salt, cost factor, and the hashed password.
In essence, bcrypt transforms your password into a highly secure hash. It’s a complex process, but it’s crucial for safeguarding your data against cyber threats.
What Are Some Other Popular Hashing Algorithms?
While bcrypt is a highly secure method for password hashing, there are several other popular algorithms you should be aware of.
First, there’s MD-5. This pioneer was designed in 1991 and gained widespread approval for its ease of use and reliability, even though it’s now considered less secure than newer algorithms.
Next is RIPEMD-160. Developed in Belgium, the RACE Integrity Primitives Evaluation Message Digest is a robust algorithm that offers a higher level of security than MD-5. However, it’s somewhat less popular due to its complexity.
Then, we’ve the SHA family of algorithms. Developed by the United States, these are considered slightly more secure than the previous two. The SHA family includes several versions, each offering varying levels of security and performance.
Whirlpool, created in 2000, is based on the Advanced Encryption Standard. It’s known for its strong security and high speed, making it a popular choice for many applications.
Lastly, there’s CRC32. This one is used primarily for detecting errors and changes in data rather than for security. Its simplicity and speed make it ideal for applications where data integrity, rather than confidentiality, is the main concern.
How Does bcrypt Compare with these hashing algorithms?
Bcrypt offers several distinct advantages compared to the aforementioned hashing algorithms.
Bcrypt isn’t just a hashing function; it’s an adaptive hash function. This means it’s designed to adjust to the increasing power of hardware.
As computer hardware evolves, bcrypt can increase its computational cost to keep pace, ensuring your data remains secure.
Unlike MD5 and SHA-1, bcrypt isn’t susceptible to rainbow table attacks. It utilizes a salt, a random value, for each password hash. This salt ensures that even identical passwords will produce unique hashes, making pre-computed tables useless.
In comparison to SHA-256 or SHA-3, bcrypt may seem slower, but that’s precisely the point.
Quick hashing algorithms are a boon for attackers who use brute force.
Bcrypt’s slower speed is an intentional design choice to add a layer of security, making brute force attacks more time-consuming and less feasible.

Why bcrypt is considered more secure?
Bcrypt is often considered as a more secure option for password hashing because of Bcrypt is adaptive function.
This means its iteration count can be increased, making it slower and hence more resistant to brute-force attacks as computation power increases. It’s not about speed, it’s about security.
Also, because Bcrypt uses a salted hash method, it adds a random data chunk, the salt, to the password before hashing. This addition makes the resulting hash unique and more complex, thwarting attempts by attackers to reverse-engineer it.
Bcrypt also has a cost parameter that you can adjust, controlling the number of iterations. This gives you the flexibility to balance between security and performance.
Finally, Bcrypt has a sterling reputation. It’s been widely used for a long time and remains unbroken. It’s robust protection against brute force and rainbow table attacks only adds to its credibility.
What are the Benefits Of Using Bcrypt?
Several advantages come with using Bcrypt for your password hashing needs.
- Its slow runtime, for example, acts as a shield against hacker attempts. By intentionally slowing down the hashing process, Bcrypt mitigates the threat of hackers using fast computers to crack your password. This feature makes it a potent tool in your cybersecurity arsenal.
- Another benefit of Bcrypt is its use of salt to generate unique and resistant password hashes. This means that even if two users have the same password, their hashes will be different, making it much harder for hackers to guess any password based on the hash alone. This makes Bcrypt a superior choice for secure password storage.
- Bcrypt also adapts to changes in hardware and software optimization. As technology evolves and computers become even faster, Bcrypt can adjust the cost factor to slow down the hashing process accordingly. This ensures that it remains secure and effective against advanced hacking attempts.
What are some Practical Applications of Bcrypt?
In your day-to-day internet use, you’re likely interacting with numerous applications that rely on Bcrypt for password security.
- For instance, WordPress, a popular content management system, employs Bcrypt in its PHP implementation for secure password storage. When you create an account or change your password, WordPress uses Bcrypt to hash your password before storing it in the database.
- Similarly, OpenBSD, a free and open-source Unix-like operating system, also utilizes Bcrypt for password hashing.
- In addition to these, many web development frameworks, such as Ruby on Rails, Django, and Laravel, include built-in Bcrypt functionality. This allows developers to easily implement secure password storage and authentication in their applications.
- Moreover, bcrypt is a crucial component in preventing brute force attacks. Its slow hashing algorithm and cost factor make it computationally expensive and thus impractical for an attacker to guess a password through sheer force of repetition.
Its practical applications extend beyond mere password safety, contributing to overall cybersecurity measures.
Best practices for using Bcrypt
Unique salts augment security by making each hashed password distinct, even if the plaintext passwords are identical. This mitigates the risk of rainbow table attacks, where precomputed tables are used to reverse cryptographic hash functions.
Setting a suitable work factor, that is, as large as your server performance allows, is paramount. A higher work factor means it takes longer to compute the hash, enhancing resistance to brute force attacks. Remember, the minimum recommended work factor is 10.
Be aware of bcrypt’s 72-byte password limit. Ensure your passwords don’t exceed this, as any extra characters are ignored, possibly leading to weaker passwords.
If working with legacy systems that use less secure hashing algorithms, it’s recommended to upgrade these hashes using bcrypt. This hashing function provides a robust defense against unauthorized access.
Frequently Asked Questions
What Are Some Common Misconceptions About Bcrypt Password Hashing Function?
You might think bcrypt password hashing function makes your data uncrackable. That’s not true. It increases security, but isn’t foolproof. Strong, unique passwords and regular updates are still necessary for optimal protection.
Are There Any Significant Drawbacks or Limitations Associated With Using Bcrypt?
Yes, bcrypt has limitations. It’s slow by design, which can impact system performance. Also, it can’t handle passwords over 72 characters, potentially forcing you to truncate longer ones, weakening your overall security setup.
How Does Bcrypt Coexist With Other Security Measures in an Overall Security Strategy?
Bcrypt coexists with other security measures by enhancing password protection. It doesn’t replace firewalls, encryption, or intrusion detection but adds a layer of security by making brute-force attacks more difficult and time-consuming.
What Future Advancements or Improvements Might We Expect to See in Bcrypt or Similar Hashing Algorithms?
You might see advancements in bcrypt or similar hashing algorithms involving increased hash lengths for better security, improved performance, or new features to counteract emerging cryptographic attacks. It’s an ever-evolving field.
Can Bcrypt Be Used in Conjunction With Other Hashing Algorithms for Added Security?
Yes, you can use bcrypt with other hashing algorithms to enhance security. It’s called “hash chaining”. However, it’s not always necessarily safer and could potentially introduce new vulnerabilities if not implemented correctly.
Bottom Line
So, you’ve learned how bcrypt’s unique features and best practices can fortify your system’s security, but let’s get to the bottom line.
In essence, bcrypt provides robust protection against brute force and rainbow table attacks, thanks to its slow-working hashing algorithm. This requires significant computational effort, thereby delaying potential attackers. Its flexible cryptographic setup adds another layer of complexity that makes it harder to crack.
However, do remember that bcrypt’s efficacy largely depends on its correct implementation, particularly the use of unique salts for each password.
🔴 READ NEXT
- What Are Sniper Bots Used in Defi Trading?
- What Are Anonymous Debit Cards And How Do They Work?
- What Is a Sim Swap Hack?
- What Is the Dencun Upgrade for Ethereum?
- What Is Batch Token Transfer And How Does It Work?
Previous Articles:
- What Are Sniper Bots Used in Defi Trading?
- Bitcoin Rally Boosts Crypto-Related Stocks as Investors Eye Spot ETF Approval
- The Four Seasons of Crypto: Navigating Bitcoin’s Market Cycles
- Gemini and DCG Face Allegations of Defrauding Investors in $1 Billion Lawsuit
- Crypto Firms Invest Heavily in Washington, Seeking Mainstream Acceptance and Favorable Regulations
