You’ve likely heard the term ‘sim-swap,’ but do you really know what it means? It’s a type of fraud that’s rapidly increasing, where scammers take control of your phone number.
Understanding how it works and its implications can help you avoid a potentially huge headache.
In this article we’re explaining what is a sim swap, dive into the mechanics of sim-swapping, discuss real-life incidents, and equip you with preventive measures to help you stay safe.
Table of Contents
What Is a Sim Swap Hack?
In the world of telecommunications, you’ve likely heard the term ‘Sim-Swap‘, but what does it actually mean?
It’s a fraudulent act where a malicious entity convinces your service provider to activate a new SIM card associated with your phone number.
They’re essentially stealing your identity, gaining access to personal data, and possibly intercepting sensitive information.
You’re left with a deactivated SIM, while they control your number. This isn’t a random act, but a targeted one.
The perpetrator likely has some of your personal information already. They’ll use this to convince the service provider they’re you.
The Mechanics of Sim-Swap Fraud
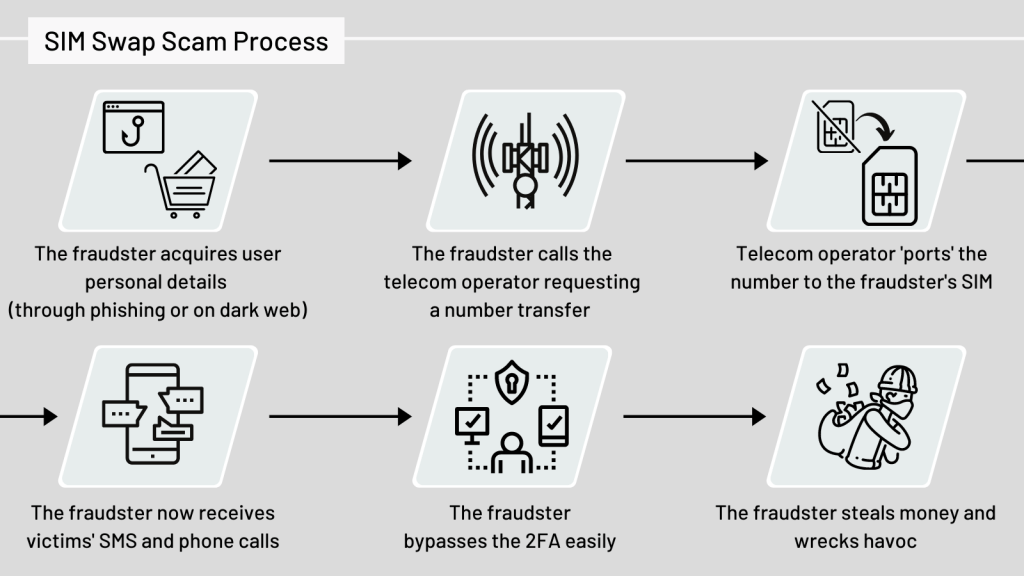
To grasp the mechanics of a Sim-Swap fraud, it’s essential to understand your attacker’s process.
The fraudster first collects personal information about you.
This could be from phishing emails, data breaches, or social engineering tactics.
Once they have your details, they contact your service provider pretending to be you, and request a sim swap.
The provider deactivates your sim and activates a new one in the fraudster’s phone.
Your calls, texts, and crucially, your verification codes, now go to them.
| Step | Action | Outcome |
|---|---|---|
| 1 | Collect Information | Fraudster has your personal details |
| 2 | Contact Service Provider | Fraudster pretends to be you |
| 3 | Request Sim Swap | Your sim is deactivated |
| 4 | Activate New Sim | Fraudster receives your calls, texts, and verification codes |
Implications of Sim-Swapping
When your sim card is swapped, you’ll face several serious implications, impacting both your personal and financial security.
The fraudster gains control of your phone number, intercepting all calls and texts, including those with sensitive information.
This breach extends to two-factor authentication codes sent via SMS, leaving your digital accounts vulnerable to unauthorized access.
Your financial details, stored in apps linked to your phone number, are now exposed.
Fraudsters can conduct transactions, drain your accounts, or make fraudulent purchases.
Personal data like emails, contacts, and photos are also at their disposal, risking identity theft.
Sim-swapping may also lead to a damaged reputation if the scammer misuses your number.
The implications are far-reaching, potentially devastating, and emphasize the importance of robust security measures.
Real-Life Sim-Swap Incidents
Over the past few years, you’ve likely heard stories about high-profile sim-swap incidents shaking up the tech world.
They’ve hit individuals and corporations alike, leading to significant losses and heightened awareness of this digital threat.
To emphasize, let’s review a few notable incidents:
| Year | Victim | Loss |
|---|---|---|
| 2016 | DeRay Mckesson | Personal data |
| 2018 | Michael Terpin | $24 million |
| 2019 | Jack Dorsey | Twitter account |
| 2020 | Gregg Bennett | $1 million |
| 2021 | Multiple US victims | $100 million |
These cases illustrate the variety of potential losses, from social media accounts to hefty financial sums.
Each incident underscores an urgent need for better security measures against sim-swapping, and serves as a stark reminder of the risks you face in our increasingly interconnected world.
Preventive Measures Against Sim-Swapping
You’ve got several effective strategies at your disposal to protect yourself from sim-swapping attacks.
- First, limit the personal information you share online. Hackers can’t use what they don’t know.
- Use two-factor authentication (2FA) for online accounts whenever possible, but avoid SMS-based 2FA due to its vulnerability to sim-swaps. Instead, opt for app-based 2FA like Google Authenticator.
- Regularly update your devices and apps to ensure you’ve the latest security patches.
- Keep your phone number private and avoid linking it to critical accounts.
- Contact your service provider and inquire about additional security measures, such as setting up a PIN or passcode that must be provided before any changes can be made to your account.
Frequently Asked Questions
What Legal Action Can Be Taken if I Become a Victim of a Sim-Swap Scam?
If you’re a victim of this scam, you can report it to your local law enforcement and the Federal Trade Commission. You’ll need to also inform your mobile provider to secure your account.
How Can I Recover My Lost Data After a Sim-Swap?
To recover your lost data after a swap, you’ll need to rely on backups. If you’ve backed up your data on a cloud service or external device, you can restore your information from there.
Can My Mobile Service Provider Be Held Liable for a Sim-Swap Fraud?
You can potentially hold your mobile service provider liable for a sim-swap fraud. However, it’ll depend on the specifics of the case, like whether they followed security protocols or if negligence was involved.
How Long Does It Typically Take to Regain Control of a Sim-Swapped Phone Number?
Regaining control of your phone number after a sim-swap can vary. It’s dependent on your service provider’s response time, but typically, it could take anywhere from a few hours to several days.
Can a Sim-Swap Affect Other Devices Linked to My Mobile Number?
Yes, a sim-swap can affect other devices linked to your number. Once swapped, the fraudster gains control, potentially accessing any device or account verified through your number. This includes emails, banking, or social media accounts.
Bottom Line
In essence, a sim-swap is a malicious act, potentially devastating to your digital life. It’s a sophisticated fraud that exploits weaknesses in two-step verification. It’s not a distant threat; real-life incidents have shown its potential damage.
But don’t fret! There are preventive measures you can take. Stay vigilant, secure your personal information, and be proactive in your digital security.
Remember, in this digital age, your online safety should be a priority.
Check more terms explanations in our Crypto Glossary page.
🔴 LATEST POSTS
- Australia Proposes Stricter Regulations for Cryptocurrency Amid Growing Adoption
- The Bahamas Embraces Innovation and Regulation in Digital Finance
- Platypus DeFi Faces Third Exploit in 2023, Suspends Pools to Address Security Concerns
- USDC Tokens Go Native on Polygon: Faster, Cheaper, and Easier
- Solana’s Milestone 1.16 Update Introduces Confidential Transfers for SPL Tokens as SOL Holds Steady
Previous Articles:
- Australia Proposes Stricter Regulations for Cryptocurrency Amid Growing Adoption
- The Bahamas Embraces Innovation and Regulation in Digital Finance
- Platypus DeFi Faces Third Exploit in 2023, Suspends Pools to Address Security Concerns
- USDC Tokens Go Native on Polygon: Faster, Cheaper, and Easier
- Solana’s Milestone 1.16 Update Introduces Confidential Transfers for SPL Tokens as SOL Holds Steady

